前言
Dynamic Trunking Protocol (DTP) 本來可以讓 Switch 與 Switch 之間方便地建立 Trunk Link,但卻成為網絡上一個可以被攻擊的弱點。本文會嘗試用 Yersinia 去攻擊 Switch 的 DTP 從而影響 VLAN 運作,假設讀者已了解 VLAN 及 DTP 的理論。
⛑️ 本文目的只為學術研究,解釋網絡漏洞及防治方法,並不鼓勵任何犯法行為,敬請留意。⛑️
Trunk Link 欺騙
在預設情況下,Switch Port 的 DTP 是被設為 Dynamic Auto 的,如果遇到對方是 Dynamic Desirable 就會由 Access Link 轉為 Trunk Link。所以 Attacker 要騙取 Trunk Link 方法很簡單,只要向 Switch Port 定時發放 Dynamic Desirable 的 DTP 訊息即可。
請看以下例子,Attacker 與 PC 分別被放在 VLAN10 和 VLAN20,不透過 Gateway 的話,理論上它們是沒法溝通的。可惜 SW1 的 Fa1/0/24 是 Dynamic Auto Mode,讓 Attacker 有機可乘。
SW1#show int fastEthernet 1/0/24 trunk Port Mode Encapsulation Status Native vlan Fa1/0/24 auto negotiate not-trunking 1 Port Vlans allowed on trunk Fa1/0/24 10 Port Vlans allowed and active in management domain Fa1/0/24 10 Port Vlans in spanning tree forwarding state and not pruned Fa1/0/24 10
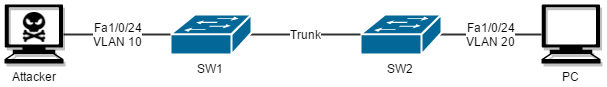
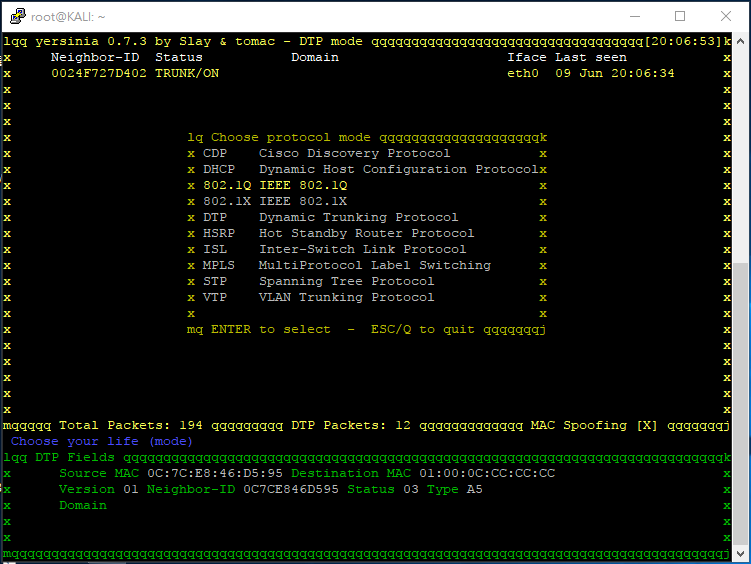
Attacker 打開 Yersinia,按 g 選 DTP 預備進行 Dynamic Trunking Protocol 攻擊。
按 x 選 1,Yersinia 就會開始發出 DTP 與 Switch 溝通並成為 Trunk。
SW1#show int fastEthernet 1/0/24 trunk
Port Mode Encapsulation Status Native vlan
Fa1/0/24 auto n-802.1q trunking 1
Port Vlans allowed on trunk
Fa1/0/24 1-4094
Port Vlans allowed and active in management domain
Fa1/0/24 1,11-20
Port Vlans in spanning tree forwarding state and not pruned
Fa1/0/24 none
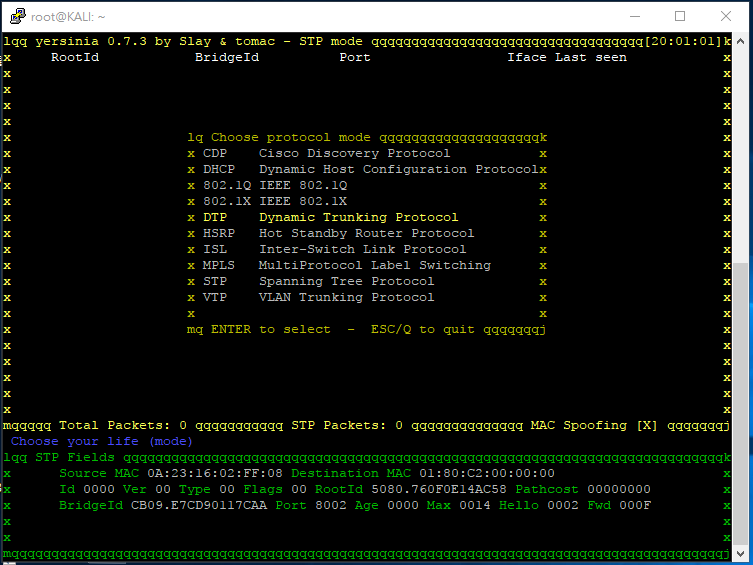
由於已經成為 Trunk Link,Attacker 可以發 Packet 到任何 VLAN,測試一下,按 g 切換到 802.1Q。
由於騷擾對像是 VLAN20,首先按 e 把 Packet 的 VLAN 修改成 20。
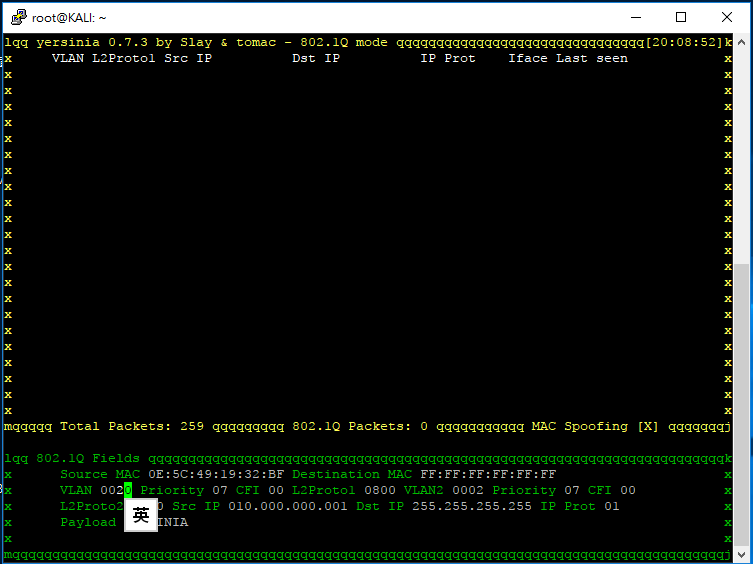
按 x 再選 0 即可發出一個 Broadcast ICMP Packet (Destination IP: 255.255.255.255) 到 VLAN20,如果在 PC 用 Wireshark 擷取的話可以清楚看到這個 Packet。
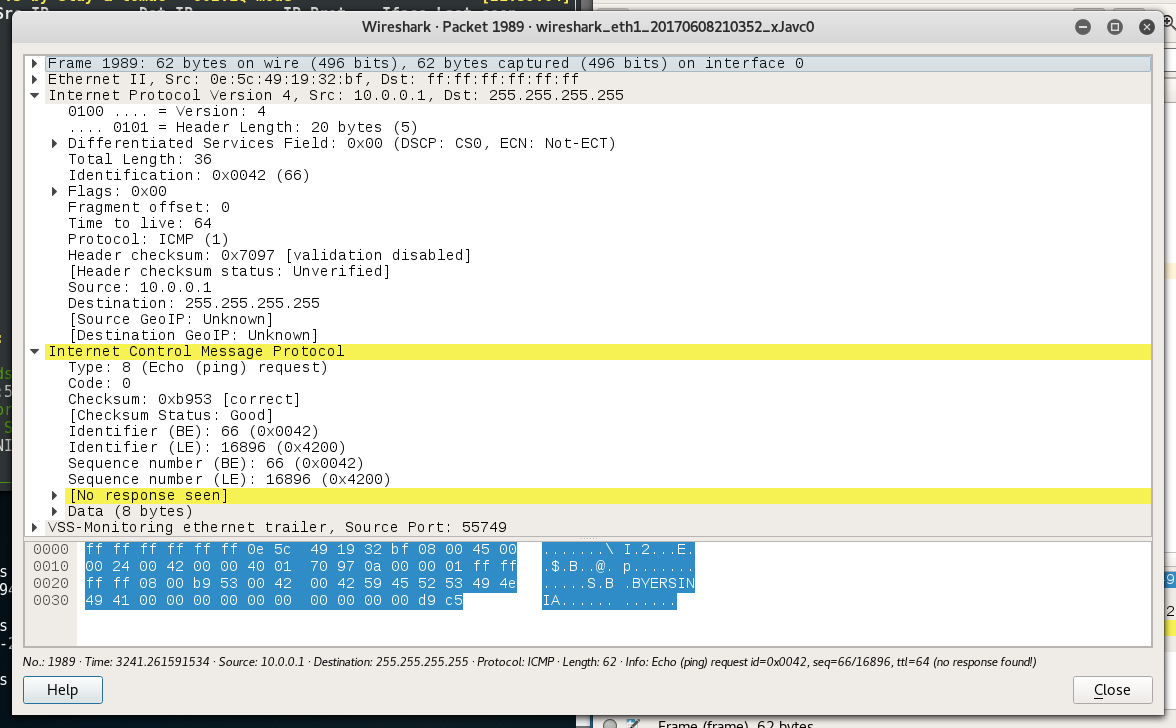
這樣,Attacker 就可以配合軟件對 VLAN20 作出 ARP Spoofing、DHCP Spoofing 或 Man-in-the-middle 等攻擊。
防禦對策
解決方法是網絡管理員要勤力一點,把連接 Host 的 Port 都關掉 DTP,即改行 Access Mode,Host 便無法與 Switch 成為 Trunk Link。
SW1(config-if)#switchport mode access
VLAN Hopping
在遠古時代,就算轉用 Access Mode,Attacker 仍有方法進行 VLAN 攻擊,稱為 VLAN Hopping Attack 或 Double Tag Attack。請看下圖,SW1 和 SW2 之間是 Trunk Link,而 Native VLAN 沒有更改過,為預設 VLAN1,剛好 Attacker 的 Access Port 也在使用 VLAN1。
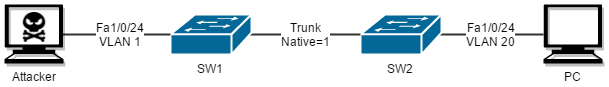
在這個巧合的情況下,Attacker 可以用 Double Tag 的方法,把 VLAN20 的訊息包裹在 VLAN1 之中傳給 SW1。由於 VLAN1 是 Native VLAN,於是 SW1 在傳給 SW2 之前會把 Packet 的 VLAN1 Tag 移除,然後才傳給 SW2。SW2 發現 Packet 中帶有 VLAN20 Tag,於是就把這 Packet 打進 VLAN20 了。
但是筆者測試過,現代的 IOS (Version 12 或以上) 已無法進行這種攻擊了。不過為了安全起見,我們習慣上都不會把 VLAN1 分派給 user 使用。
相關主題
Jan Ho 2017-06-10
Posted In: 網絡破解技術 Hacking
發佈留言