目錄
前言
Bandwidth Management (頻寬管理) 常見於企業與服務供應商 (ISP) 之間的網絡連線,當 Interface Speed 大於供應商所承諾的 Committed Information Rate (CIR),則企業網管人員需主動限制輸出頻寬。學習 Bandwidth Management 主要在於兩個範疇:Traffic Shaping 和 Traffic Policing。本篇文章會先探討 Bucket 與 Token 原理,再闡述 Traffic Shaping 和 Traffic Policing 的設定。
需要 Bandwidth Management 的原因
用以連接 Remote Site 的 Point-to-Point 或 Point-to-Multipoint 連線頻寬一般成本較高,ISP 只能提供不高於 CIR 的服務保證,超出 CIR 的 Traffic 就不會保證能否送達目的地了,也有可能需要為額外使用的頻寬收費。因此,網管人員應實施有效的 Bandwidth Management 去限制 Bandwidth 使用量。
Bandwidth Management 的原理
Bandwidth Management 的原理很簡單!只要 ISP 告訴我們 CIR 限制是多少,我們就把 Interface 的傳輸速度壓下去,這就成功了!好像很廢話!請先看下圖,例如:一個速度 10 Mbps 的 Interface,CIR 只容許 2 Mbps。
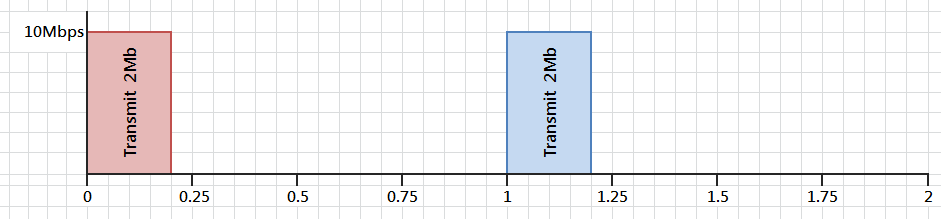
如圖所見,Interface 以 1 秒為間距,每 1 秒只容許傳輸 2 Mbits,傳夠 2 Mbits 後便停止傳送,然而 Interface 以 10 Mbps 的速度工作,只需 0.2 秒便完成 2 Mbits 的數據傳輸,然後等待 0.8 秒才再做下一次傳送。問題是:0.8 秒的等待時間實在太久了,用 VoIP 作例子,持續的 VoIP Packet 之間不應相距多於 100 ms (0.1 秒)。VoIP Packet 多被 QoS 設定為高重要性,所以可以幻想得到在每一次的傳輸,VoIP Packet 都被安排在較前列位置,可惜每隔 0.8 秒才獲得一次傳輸機會對 Voice Traffic 帶來重大影響。
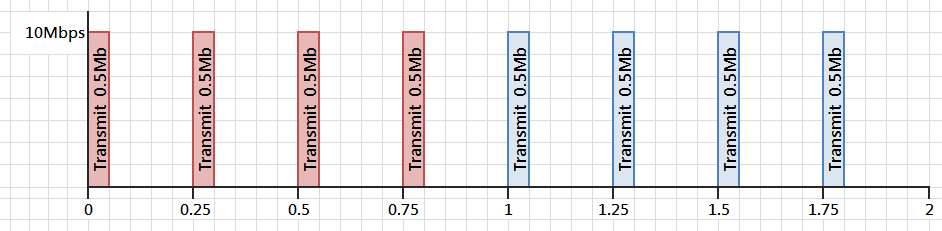
如果把間距由 1 秒縮短至 0.25 秒,每段間距改成只限制傳輸 0.5 Mbits。有趣的是:這改變一樣可以達成每秒傳輸 2 Mbits 這個限制,但每次傳送的相距時間卻可大幅降低。
Bucket and Token Algorithm
為了更加實體化,我們一般會使用 Bucket and Token 去解釋 Bandwidth Management。在 Bucket and Token Algorithm 裡,Interface 每傳送 1 Bit,必需從 Bucket 消耗一粒 Token,如果 Bucket 裡沒有 Token 則不容許傳送。每隔一定時間 (Time Interval Tc),系統就會向 Bucket 補充一定數量 (Committed Burst Bc) 的 Token。以上圖為例,系統每隔 0.25 秒就向 Bucket 注入 50 萬粒 Token,而 Bucket 的容量剛好也等於 Committed Burst Bc,滿瀉的 Token 會被移除,這意味著 Interface 在未來 0.25 秒內最多只能傳送 0.5 MBits (500,000 Bits) ,這就可以確保傳輸速度不會超過限額。
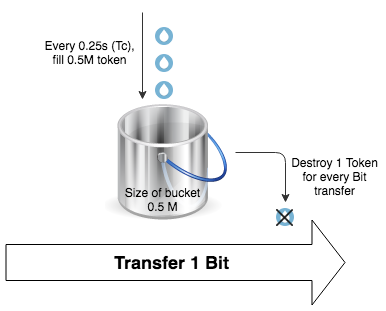
所以當 ISP 告訴我 CIR 是 2 Mbps,假若我們把 Committed Burst Bc 設定成 500,000 Bits,系統就會很容易計算出 Time Interval Tc 是 0.25 秒,即每秒有 4 次注入 Token 的循環。公式如下:
Bc 的大小是可以自行決定的,從剛才的例子可見,Bc 的 Size 太大,間距增長導致 Delay 增加,那麽把 Bc 設定成細小的值,情況又會怎樣呢?今次我們以 Interface Speed 10 Mbps,設定 CIR 為 1 Mbps 去傳送一個 1,500 Bytes (12,000 Bits) 的 Packet 作例子,計算一下使用不同 Bc 的傳送時間。
1. 如 Bc = 900,Tc = 900/1,000,000=0.0009 秒
2. 以 Packet Size 12,000 除 900 得出要傳送完成需要 13 個循環再多一點點。
3. 13 個循環所需時間為 13 x 0.0009 = 0.0117 秒,即 0.0117 秒傳送了 13 次 900 Bits,共 11,700 Bits,剩餘的 300 Bits 就要等待下一次循環了。
4. 到了第 14 個循環,Interface 以 10 Mbps 的速度把剩餘的 300 Bits 傳送,共使用:300/10,000,000 = 0.00003 秒
5. 因此整個傳送過程共用了 0.0117+0.00003=0.01173 秒,這個由 Packet 開始被傳送至到完成傳送的時間可稱之為 Lead Time。
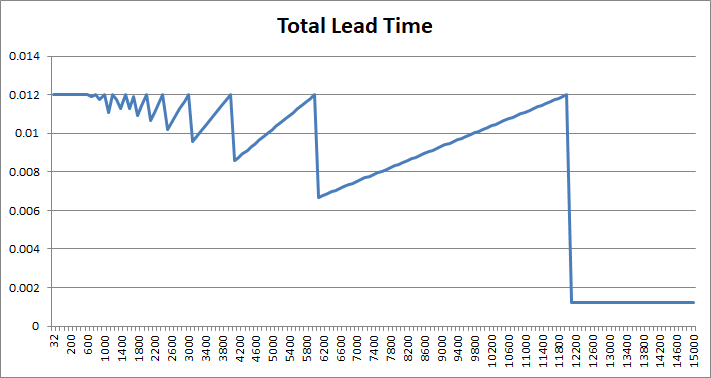
只要計算不同 Bc 所得出的 Lead Time,可得出下圖,從圖中可見,不同 Bc 之 Lead Time 相距甚遠,可以有數倍之差。當 Bc 增加至與 Packet Size 相等時 (12,000 Bits),Lead Time 變得較少。由此可見,把 Bc 設定成與 Packet Size 相等是一個很好的選擇。但問題是,網絡上 Traffic 的 Packet Size 千變萬化,我們需要估算一下什麼 Traffic 比較多和重要,如果網絡大部份 Traffic 是 VoIP,則可把 Bc 設成 RTP 的 Payload Size,例如:G711 是 160 Bytes。如果 Traffic 以大 Size 的 File Transfer 為主,則可設成一般系統的 Maximum Transmission Unit (MTU) 1,500 Bytes。
Traffic Shaping
如果看到這裡你還應付得來的話,我們便可以開始討論 Traffic Shaping 了。所謂 Shaping 的意思很簡單,就是把超出 CIR 的 Packet 暫時放在一個 Buffer 之中等待一下,到情況許可時再傳送出去,這樣就可以低成本地和更有效率地使用 Bandwidth。從下圖可以看到 Shaping 後的 Traffic 看起來比較平整,尖峰被削掉並安排在較後時間輸出。
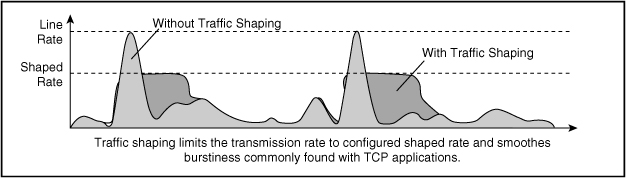
Class-based Shaping
以下介紹一個最基本的 Shaping 設定。
第一步:設定 Policy Map。Keyword class-default 意思是所有未分類的 Traffic,由於我們並沒有做 QoS Classification,所以這裡的意思就是把所有 Traffic 來做一個 Shaping 設定。當然我們可以為不同的 Traffic 類型分別做不同的 Shaping 設定,但很少會這樣處理,因為我們通常會為不同的 Traffic Class 做了 CBWFQ 和 LLQ 等設定來限制其 Bandwidth。關於 Classification 和 QoS 設定將會在日後介紹 QoS 的文章中再詳細說明。
Shape 指令第一個選項請選 average (稍後說明),然後第二個選項是要限制的 CIR,第三個選項就是 Committed Burst Bc,最後是 Excess Burst Be 暫時設為 0 (稍後說明)。
R2(config)#policy-map SHAPE-TO-1M R2(config-pmap)#class class-default R2(config-pmap-c)#shape average 1m 12000 0
第二步:把 Policy Map 放到 Outgoing Interface。
R2(config)#int ethernet 1/1 R2(config-if)#service-policy output SHAPE-TO-1M
用 show policy-map interface 指令查看結果。
R2#show policy-map interface ethernet 1/1
Ethernet1/1
Service-policy output: SHAPE-TO-1M
Class-map: class-default (match-any)
7944 packets, 7651699 bytes
5 minute offered rate 20000 bps, drop rate 0000 bps
Match: any
Queueing
queue limit 64 packets
(queue depth/total drops/no-buffer drops) 0/2/0
(pkts output/bytes output) 7944/7651699
shape (average) cir 1000000, bc 12000, be 0
target shape rate 1000000
Committed Burst 與 Excess Burst
一切設定好後,本來以為可以休息一下,突然你又收到 ISP 銷售人員來電,告訴你不如多付一點點錢,他們便容許你在必要時提升 Bandwidth,這又是什麼回事呢?原來 ISP 的連線和網絡設備在同一時間正招呼不同的顧客,每位顧客都擁有自己的 CIR,但 ISP 知道不可能每位顧客都在同一時間用到 CIR 的上限,所以他們還有空間把非繁忙時間剩餘的 Bandwidth 賣出去,稱為 Over-subscription。於是他們介紹你一個新計劃,除了那 1 Mbps 的保證服務外,你還可以使用額外 0.5 Mbps,但使用這些額外 Bandwidth 的 Traffic 只能在網絡暢通時送達。於是網管人員該怎樣修改 Shaping 設定呢?
我們再拿水桶圖出來解說一下,左面是原設定。如要使用額外頻寬,我們可以把 Bucket 的 Size 加大,讓它可以裝載更多的 Token,留意補充 Token 的速度並無改變,可以幻想得到,在 Traffic 量少時,Token 便會被貯起來,最終能貯至 Bc + Be。假設把 Be 設成 6,000,當 12,000 + 6,000 Token 在同一循環被使用時,該時刻的理論 Bandwidth 達 18,000/0.012 = 1.5 Mbps,然而平均 Bandwidth 卻從來沒有改變,因為 Token 補充速度沒有改變,這就好像把用不完的 Bandwidth 先貯起來,到有需要時一次過爆發。
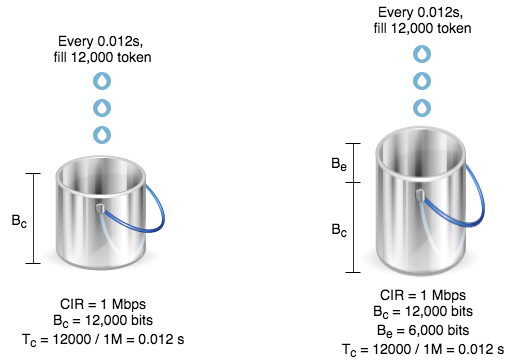
修改 Be 設定如下:
R2(config)#policy-map SHAPE-TO-1M
R2(config-pmap)#class class-default
R2(config-pmap-c)#shape average 1m 12000 6000
R2#show policy-map interface ethernet 1/1
Ethernet1/1
Service-policy output: SHAPE-TO-1M
Class-map: class-default (match-any)
16123 packets, 15515474 bytes
5 minute offered rate 19000 bps, drop rate 0000 bps
Match: any
Queueing
queue limit 64 packets
(queue depth/total drops/no-buffer drops) 0/4/0
(pkts output/bytes output) 16123/15515474
shape (average) cir 1000000, bc 12000, be 6000
target shape rate 1000000
PIR (Peak Information Rate)
我們還可以進一步把補充 Token 的水量加大,更進取地使用額外 Bandwidth。只要把 Shape 指令裡的 keyword average 換成 peak,則 Token 補充量變為 Bc + Be,在 Tc 不改變的情況下,傳輸頻寬因而變大,亦稱為 PIR (Peak Information Rate)。
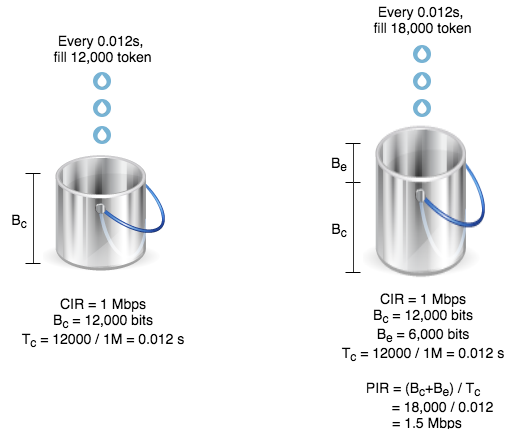
設定如下:
R2(config)#policy-map SHAPE-TO-1M
R2(config-pmap)#class class-default
R2(config-pmap-c)#shape peak 1m 12000 6000
R2#show policy-map interface ethernet 1/1
Ethernet1/1
Service-policy output: SHAPE-TO-1M
Class-map: class-default (match-any)
19117 packets, 18386110 bytes
5 minute offered rate 19000 bps, drop rate 0000 bps
Match: any
Queueing
queue limit 64 packets
(queue depth/total drops/no-buffer drops) 0/4/0
(pkts output/bytes output) 19117/18386110
shape (peak) cir 1000000, bc 12000, be 6000
target shape rate 1500000
網管人員需注意 ISP 只為 CIR Bandwidth 作保證傳輸,超過 CIR 則有機會被 Drop 或 Delay,考慮以上因素才決定使用那一種設定。
queue-limit
剛開始介紹 Shaping 時有提過 Packet 等待傳送時會被儲存在 Buffer 之中,此 Buffer 也稱為 queue-limit,容量可以調校。Packet 會在這 Buffer 裡排隊等候傳送,但如果 queue-limit 爆滿,則會發生 Tail Drop,即後來想進入 Buffer 的 Packet 會被 Drop 掉,除非使用了 WRED,這又是 QoS 的話題,在稍後關於 QoS 的文章再說明。修改 queue-limit 指令如下:
R2(config-pmap-c)#queue-limit 200
R2#show policy-map interface ethernet 1/1
Ethernet1/1
Service-policy output: SHAPE-TO-1M
Class-map: class-default (match-any)
27918 packets, 26846162 bytes
5 minute offered rate 20000 bps, drop rate 0000 bps
Match: any
Queueing
queue limit 200 packets
(queue depth/total drops/no-buffer drops) 0/4/0
(pkts output/bytes output) 27918/26846162
shape (peak) cir 1000000, bc 12000, be 6000
target shape rate 1500000
修改 queue-limit 時除了可用 Packet 作單位外,也可以容量 Bytes 和時間 ms 或 us 作單位。如使用時間作單位,則系統會以 [CIR x 時間] 計算出 Bytes,這很實用,例如:網絡以傳送 Live Video 為主,基本上超過 1 秒 delay 的影像 Payload 對 Client 來說已經沒有意義了,倒不如把 queue-limit 定在 1000ms,這就能把超出 1 秒 Delay 的 Packet Drop 掉,留些空間給未來的影像 Payload 進入 queue。
R2(config-pmap-c)#queue-limit 1000 ms
R2#show policy-map interface ethernet 1/1
Ethernet1/1
Service-policy output: SHAPE-TO-1M
Class-map: class-default (match-any)
30041 packets, 28890083 bytes
5 minute offered rate 20000 bps, drop rate 0000 bps
Match: any
Queueing
queue limit 1000 ms/ 125000 bytes
(queue depth/total drops/no-buffer drops) 0/4/0
(pkts output/bytes output) 30041/28890083
shape (peak) cir 1000000, bc 12000, be 6000
target shape rate 1500000
修改 queue-limit 需注意如果 queue-limit 值太短可能會觸發不必要的 QoS Congestion Management (未來 QoS 文章中再解說),相反如果 queue-limit 太長則會導致 Packet 在 queue 裡等太久而發生 delay 問題。
Traffic Policing
現在我們換個身份,變成 ISP 那邊的網管人員,雖然我們已告訴客戶 CIR 或 PIR,但我們無法保證客戶有乖乖的做好 Bandwidth Management,他們可能把超額的 Traffic 硬塞過來給我們。因此作為 ISP 的一方必需做好我們自家的 Bandwidth Management,去好好處理客戶硬塞過來的 Traffic。ISP 用的不會是 Shaping,試想想,Traffic 已經來到我的 Interface 了,進來的 Traffic 必需盡快處理掉,要傳送或是丟棄還是做其他動作?這要靠 Traffic Policing 設定去決定。Traffic Policing 與 Traffic Shaping 相似的地方是一樣用到水桶理論,但很玩野的是:Policing 的 Token 單位是 Bytes 而不是 Bits。另外,Policing 不會作延時傳送,Token 的足夠與否所決定的是對 Packet 的政策 (即 Policy),也稱為顏色 (Color)。Traffic Policing 一共有 3 種:分別是 Single-rate Two-color Policer、Single-rate Three-color Policer 與及 Two-rate Three-color Policer (或稱 Dual-rate Three-color Policer)。
Single-rate Two-color Policer
透過查看 Bc Bucket 是否有足夠 Token 來作出判斷執行綠色動作 (Conform Action) 還是紅色動作 (Exceed Action),Action 是可以自訂的,選項包括:傳送 (Transmit)、丟棄 (Drop) 或者重新標記 (Remark)。
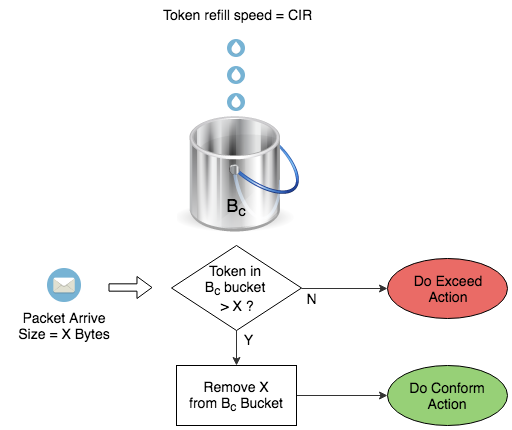
以下 Policing 設定把 CIR 設為 1 Mbps,Bc 設為 1500 Bytes,Conform Action 設為 Transmit,Exceed Action 設為 Drop。透過這設定,客戶傳過來的流量一旦超過了雙方協議的 CIR,就會開始被 Drop 掉。
R3(config)#policy-map ONE-RATE-TWO-COLOR R3(config-pmap)#class class-default R3(config-pmap-c)#police cir 1000000 bc 1500 R3(config-pmap-c-police)#conform-action transmit R3(config-pmap-c-police)#exceed-action drop R3(config-pmap-c-police)#exit R3(config-pmap-c)#exit R3(config-pmap)#exit R3(config)#int ethernet 1/0 R3(config-if)#service-policy input ONE-RATE-TWO-COLOR
R3#show policy-map interface ethernet 1/0
Ethernet1/0
Service-policy input: ONE-RATE-TWO-COLOR
Class-map: class-default (match-any)
42 packets, 41468 bytes
5 minute offered rate 1000 bps, drop rate 1000 bps
Match: any
police:
cir 1000000 bps, bc 1500 bytes
conformed 27 packets, 18758 bytes; actions:
transmit
exceeded 15 packets, 22710 bytes; actions:
drop
conformed 1000 bps, exceeded 1000 bps
Single-rate Three-color Policer
增加 Be Bucket,從 Bc 滿瀉的 Token 會被移到 Be Bucket。透過查看兩個 Bucket 是否有足夠 Token 來作出判斷執行綠色動作 (Conform Action)、黃色動作 (Exceed Action) 還是紅色動作 (Violate Action)。與 Single-rate Two-color Policer 不同的是,Single-rate Three-color 可以對超額流量提供一定程度的容忍,例如用 Remark 的方法降低其重要性並嘗試傳送。
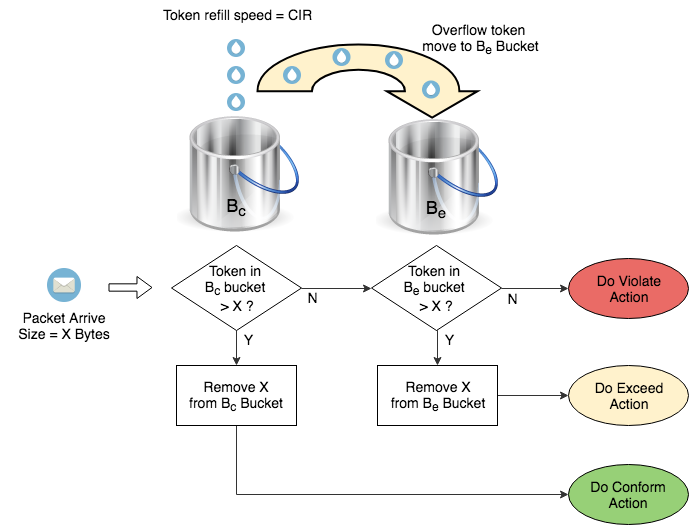
以下 Policing 設定加入了 Be 設定使其成為 Single-rate Three-color,Exceed Action 設為 set-dscp-transmit af23 表示 Packet 會被更改 DSCP 才傳送。(DSCP 原理將會在 QoS 文章中詳細說明)
R3(config)#policy-map ONE-RATE-THREE-COLOR R3(config-pmap)#class class-default R3(config-pmap-c)#police cir 1000000 bc 1500 be 1500 R3(config-pmap-c-police)#conform-action transmit R3(config-pmap-c-police)#exceed-action set-dscp-transmit af23 R3(config-pmap-c-police)#violate-action drop R3(config-pmap-c-police)#exit R3(config-pmap-c)#exit R3(config-pmap)#exit R3(config)#int ethernet 1/0 R3(config-if)#service-policy input ONE-RATE-THREE-COLOR
R3#show policy-map interface ethernet 1/0
Ethernet1/0
Service-policy input: ONE-RATE-THREE-COLOR
Class-map: class-default (match-any)
21 packets, 21446 bytes
5 minute offered rate 1000 bps, drop rate 1000 bps
Match: any
police:
cir 1000000 bps, bc 1500 bytes, be 1500 bytes
conformed 13 packets, 9334 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
set-dscp-transmit af23
violated 8 packets, 12112 bytes; actions:
drop
conformed 1000 bps, exceeded 0000 bps, violated 1000 bps
Two-rate Three-color Policer
Two-rate Three-color 比起 Single-rate Three-color 不同的地方是 Be Bucket 透過 PIR 補充,而非來自滿瀉的 Bc Bucket。這設定能準確判斷 Traffic 是否已超出 CIR 而落入 PIR 範圍,並執行相應動作。
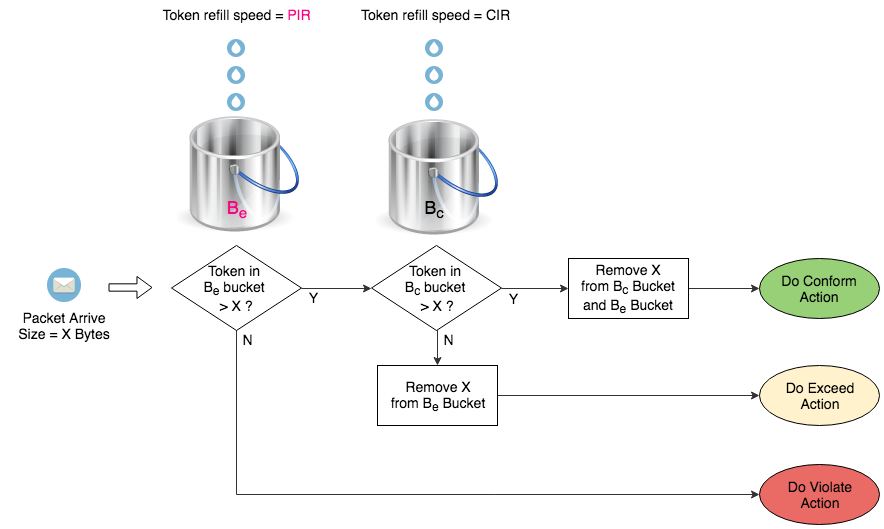
以下 Policing 設定加入了 PIR 設定使其成為 Two-rate Three-color。
R3(config)#policy-map TWO-RATE-THREE-COLOR R3(config-pmap)#class class-default R3(config-pmap-c)#police cir 1000000 bc 1500 pir 1500000 be 1500 R3(config-pmap-c-police)#conform-action transmit R3(config-pmap-c-police)#exceed-action set-dscp-transmit af23 R3(config-pmap-c-police)#violate-action drop R3(config-pmap-c-police)#exit R3(config-pmap-c)#exit R3(config-pmap)#exit R3(config)#int ethernet 1/0 R3(config-if)#service-policy input TWO-RATE-THREE-COLOR
R3#show policy-map interface ethernet 1/0
Ethernet1/0
Service-policy input: TWO-RATE-THREE-COLOR
Class-map: class-default (match-any)
83 packets, 84250 bytes
5 minute offered rate 3000 bps, drop rate 3000 bps
Match: any
police:
cir 1000000 bps, bc 1500 bytes
pir 1500000 bps, be 1500 bytes
conformed 51 packets, 35802 bytes; actions:
transmit
exceeded 0 packets, 0 bytes; actions:
set-dscp-transmit af23
violated 32 packets, 48448 bytes; actions:
drop
conformed 3000 bps, exceeded 0000 bps, violated 3000 bps
相關主題
Jan Ho 2018-04-14
Posted In: 網絡服務 Services
發佈留言