目錄
前言
關於 Multicast,本網已討論過用在 Layer 3 範疇的 PIM (Protocol Independent Multicast) 這款 Router 之間用作 Multicast Routing 的 Protocol。而在 Layer 2 的範疇,則有 IGMP (Internet Group Management Protocol) 負責 Host 與 PIM Router 之間的互動。筆者建議讀者先對 PIM 有基本認識才研讀 IGMP,因為 PIM 是 Multicast 的源頭,而 IGMP 則是 Multicast 的最下游,從源頭開始了解會比較容易消化和吸收。
IGMP 的運作原理
假設 Multicast Traffic 已經從源頭經過 PIM Network 來到 Layer 3 的最後一隻 PIM Router,問題是 Router 也不只有一個 Interface,到底那個 Interface 的 Host 需要 Multicast Traffic?還是全部都需要? IGMP 的作用就是 Host 和 Router 之間溝通的語言,透過使用 IGMP,Router 可以知道那些 Host 需要什麼 Multicast Group。
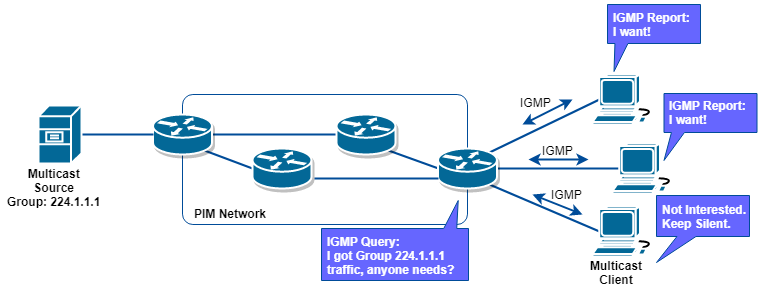
原理很簡單,當 Router (IGMP Querier) 手上有收到一些 Multicast Group 時,它便會發 Query 訊息問有沒有 Host 需要此 Group?如有 Host (Receiver) 需要,它會回應 IGMP Membership Report 訊息,Router 便知道有 Host 需要了,因此會把 Multicast Traffic 傳過去相對的 Interface,相反如果 Host 沒有回應,Router 知道沒有 Host 需要該些 Group 了,就可以不傳送 Multicast Traffic 到該 Interface 了。
而 IGMP 共有 3 個 Version,分別是 Version 1、Version 2 及 Version 3。
IGMP Version 1
使用 IGMP Version 1 的 Router 預設每 60 秒 (query-interval) 發送 Membership Query 查詢有沒有 Host 需要它手上的 Group,Host 收到後,如果需要則回應 IGMP Membership Report。如 Router 能在 Max Response Time (預設 10 秒) 內收到回覆,則判斷有 Host 需要 Multicast Group。當 Host 表示需要 Multicast Group 後,仍需於每次 Router 發送 IGMP Membership Query 時回覆以維持其對 Multicast Group 的需要。相反,如 Host 不再需要 Multicast Group,只需忽略來自 Router 的 Query,如 Router 發了 Query 後過了 180 秒都沒有收到 IGMP Membership Report 的話則 Router 判斷 Host 已不再需要此 Group。另外,Host 亦能隨時主動發送 IGMP Membership Report 給 Router 要求接收某 Group。Router 修改 query-interval 方法如下。
R1(config-if)#ip igmp query-interval 120
IGMP Version 2
Version 2 比 Version 1 進步的地方是新增了 Leave Group Message,即 Host 決定不需接收 Multicast Group 時可以發 Leave Group Message 給 Router。當 Router 收到 Leave Group Message 後,會每隔 Last-member-query-interval (預設 1000ms) 送出一個 Last-member-query,去詢問有沒有 Host 仍需要此 Group。Query 總次數由 Last-member-query-count 控制,預設為 2 次。即是說當 Router 收到 Leave Group Message 後會送出第一個 Last-member-query,然後數到 1000ms 再送出第二個,如兩個 Last-member-query 都收不到回應則判斷該 Interface 已經沒有 Host 需要該 Multicast Group。更改 Last-member-query-interval 及 Last-member-query-count 的指令如下。
R1(config-if)#ip igmp last-member-query-interval 2000 R1(config-if)#ip igmp last-member-query-count 4
如果我們確定該 Interface 只有一隻 Host,亦可要求 Router 在收到某些 Group 的 Leave Group Message 時不送出 Last-member-query 直接判斷該 Interface 所有 Host 已 Leave Group。
R1(config)#access-list 1 permit 224.1.1.1 R1(config)#int eth1/0 R1(config-if)#ip igmp immediate-leave group-list 1
此外,從 Version 2 開始亦可改變 Max Response Time,也優化了 Router 對 Multicast Group 的判斷。修改 Max Response Time 指令如下。
R1(config-if)#ip igmp query-max-response-time 20
IGMP Version 3
而 Version 3 則可支援 Source Specific Multicast (SSM),讓 Host 可以選擇接收特定 Source Address 的 Multicast Traffic。有關 SSM 的詳情,請觀看 PIM 教學文件。
啟動 IGMP
作為 IGMP Querier 的一方,Router 只需要執行了 PIM,則 IGMP 會自動啟動。至於 Receiver 方面,如果我們想在做實驗時利用 Router 來充當 Multicast Client,則可使用 ip igmp join-group 來啟動 IGMP,並用 ip igmp version 來設定 Version,預設為 Version 2。
R2(config-if)#ip igmp join-group 224.1.1.1
R2(config-if)#ip igmp version ?
version number
R2(config-if)#ip igmp version 2
最後我們可以用 show ip igmp interface 查詢 IGMP 的 Version 及 Timer 等資訊。
R2#show ip igmp interface ethernet 1/0
Ethernet1/0 is up, line protocol is up
Internet address is 192.168.12.2/24
IGMP is enabled on interface
Current IGMP host version is 2
Current IGMP router version is 2
IGMP query interval is 60 seconds
IGMP configured query interval is 60 seconds
IGMP querier timeout is 120 seconds
IGMP configured querier timeout is 120 seconds
IGMP max query response time is 10 seconds
Last member query count is 2
Last member query response interval is 1000 ms
Inbound IGMP access group is not set
IGMP activity: 1 joins, 0 leaves
Multicast routing is disabled on interface
Multicast TTL threshold is 0
Multicast groups joined by this system (number of users):
224.1.1.1(1)
IGMP Querier
Router 經常會發 IGMP Query 到網絡與 Host 溝通,試想想如同一網段中有兩隻或以上的 PIM Router 存在,它們可能擁有相同的 Group 而發放重覆的 Query Message,這是多餘的。因此同一網段中只有一隻 Router 被選為 IGMP Querier,確保 Query Message 不重覆。IGMP Version 1 會選 PIM Designated Router 為 IGMP Querier,而 IGMP Version 2 及 Version 3 則會選 Interface IP Address 較小的成為 IGMP Querier。關於 PIM Designated Router 的設定,可到 PIM 教學文件查詢。
當選定 IGMP Querier 後,一旦 Querier 失聯,其他 Router 會等待 Querier-timeout 後重新進行 Querier 選舉,Querier-timeout 預設為 IGMP Query-interval 的兩倍,即 120 秒,設定 Querier-timeout 指令如下。
R2(config-if)#ip igmp querier-timeout 100
Multicast Group 的 MAC Address
眾所周知,Router 會把 Unicast Traffic 的 Destination IP Address 1 對 1 地轉換成 MAC Address,然後把訊息發到網絡,網絡上擁有此 MAC Address 的設備便可以接收並處理此訊息。然而,Multicast Traffic 沒有 Destination IP Address,只有 Group 來代表多於一個 Destination,Router 該如何處理呢?
原來當 Multicast Packet 被建立時,已即時用 Group Address 去產生一個 MAC Address 寫在 Packet 之中。舉例,把 Group 224.1.2.3 轉換成 MAC Address 的方法如下。
Step 1:
首先把 224.1.2.3 轉換成二進制:11100000.00000001.00000010.00000011
Step 2:
只保留最後 23 Bits:0000001.00000010.00000011
Step 3:
在前面補上一串 25 Bits 的 Multicast MAC Prefix:00000001.00000000.01011110.0
00000001.00000000.01011110.00000001.00000010.00000011
Step 4:
用 16 進制表示:0100.5e01.0203
由於 Multicast Address (即 Class D,首 4 Bits 1110) 的 IP 範圍是 224.0.0.0 至 239.255.255.255,這個轉換機制會讓某些 Group 出現相同的 MAC Address 結果,同一網絡裡應避免同時使用這些 Group。
224.1.2.3 ➡️ 0100.5e01.0203
224.129.2.3 ➡️ 0100.5e01.0203
225.1.2.3 ➡️ 0100.5e01.0203
225.129.2.3 ➡️ 0100.5e01.0203
.
.
.
239.129.2.3 ➡️ 0100.5e01.0203 (共 32 組相同結果)
Router 用以上方法作轉換,而 Client Join Multicast Group 時亦使用同一套機制計算出自己需要聆聽的 MAC Address,於是當 Multicast Traffic 到達時 Client 便懂得接收和處理。
IGMP Snooping
好!問題來了,如果在 Router 與 Client 之間加入一隻 Switch,本來 Switch 是透過 Host 送出訊息時查看 Unicast 信息中的 Source MAC Address 來 Learn Host 位置,但 Host 絕不會用 Multicast Group MAC Address 來發訊息以致這些 MAC Address 無法被 Learn,因而 Switch 無法用處理 Unicast 的方法傳送 Multicast。
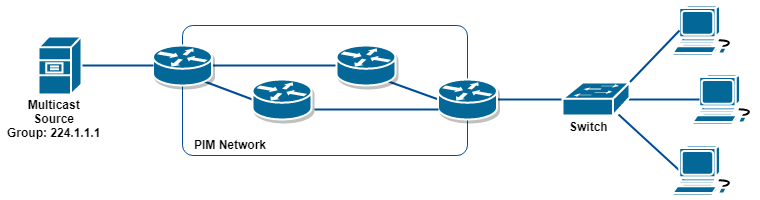
要解決這個問題,Switch 大可把 Multicast Traffic 在所有 Port 送出 (如同 Broadcast),但這麽一來就浪費 Bandwidth 了。所以比較有效的方法為 IGMP Snooping。IGMP Snooping 的原理很簡單,Switch 會持續偷聽 Host 傳給 Router 的 Join 和 Leave Message,如有 Join 出現則把 Port 加到 Snooping Table,而收到 Leave 的話則把其移除,於是 Switch 便可按 Snooping Table 判斷那個 Port 需要什麼 Group。IGMP Snooping 在 Switch 預設是啟動的,使用 show ip igmp snooping groups 可查看 Snooping Table。
Switch#show ip igmp snooping groups Vlan Group Type Version Port List ----------------------------------------------------------------------- 1 224.0.1.40 igmp v2 Gi1/0/1 1 224.1.1.1 igmp v2 Gi1/0/2 1 239.255.255.250 igmp v2 Gi1/0/11
IGMP Filtering
簡單來說,IGMP Filtering 可分為在 Router 做還是在 Switch 做。
在 Router 做的 Filtering 叫 IGMP access-group,可以用 access-list 控制 Router 只接受或不接受某些 Multicast Group, 舉例:如想 Router 不接受 Client Join Group 224.1.1.1,設定如下:
R1(config)#access-list 1 deny 224.1.1.1 R1(config)#access-list 1 permit any R1(config)#int eth1/0 R1(config-if)#ip igmp access-group 1
這樣子傳給 Router 的 Join 224.1.1.1 將不會成功,開 debug ip igmp 的話應可看到 deny 訊息。
R1#debug ip igmp IGMP debugging is on R1# *Mar 19 12:22:10.773: IGMP(0): Received v2 Report on GigabitEthernet8 from 192.168.123.2 for 224.1.1.1 *Mar 19 12:22:10.773: IGMP(*): Group 224.1.1.1 access denied on GigabitEthernet8
而在 Switch 做的 Filtering 叫 IGMP Profile,可阻隔所有流經該 Switch 的 IGMP Join 訊息。例如要阻隔所有 Join Group 224.1.1.1 至 224.1.1.255 訊息,設定如下:
SW1(config)#ip igmp profile 1 SW1(config-igmp-profile)#deny SW1(config-igmp-profile)#range 224.1.1.1 224.1.1.255 SW1(config-igmp-profile)#exit SW1(config)#int f0/1 SW1(config-if)#ip igmp filter 1
打開 debug,收到不合法 igmp join 時會收到以下訊息。
SW1(config)#debug ip igmp IGMP debugging is on SW1# Mar 19 11:11:20.359: IGMPFILTER: igmp_filter_process_pkt() checking group from Gi1/0/1 : no profile attached
相關主題
Jan Ho 2018-03-24
Posted In: Layer 2 網絡技術
發佈留言