目錄
前言
越来越多公司用 IPSEC 来建立 Site to Site VPN,普遍应用於透过 Internet 建立连线,因为价钱便宜,设定上相对简单得多。IPSEC VPN 用 IKE (Internet Key Exchange) 进行参数交换和建立连线,因此在设定 IPSEC VPN 前应先了解 IKE 的运作。
IKE (Internet Key Exchange)
IKE 又分为 Phase 1 和 Phase 2,现在来看看 Phase 1 和 Phase 2 分别做了些什麽。
Phase 1
IKE Phase 1 的工作主要是认证 (authenticate) 对方,什麽是认证呢?很简单,我是 Site A 的 Router,你说你是 Site B 的 Router 想和我建立 VPN,我怎知道你真的是 Site B 而不是其他公司呢?其中一个常用的方法是用 Share Secret 来认证,即是说 Site A 和 Site B 的 Router 都知道同一组密码,证明是自己人,就通过认证了。另外,Phase 1 还会用透过 Diffie-Hellman 来建立一组 Key,这组 Key 是用来为 Phase 2 的资讯进行加密,即是说 Phase 1 的工作就是为 Phase 2 准备一条加密管道,让 Phase 2 用这条管道去交换资讯。
Phase 2
至於 Phase 2 则是真正建立 IPSEC VPN 管道让资讯在这条管道上传送。记着 Phase 2 是建立在 Phase 1 之上的,没有 Phase 1 就没有 Phase 2。
设定
现在我们试为以下网络的 Site A 和 Site B 设定 Site to Site IPSEC VPN。
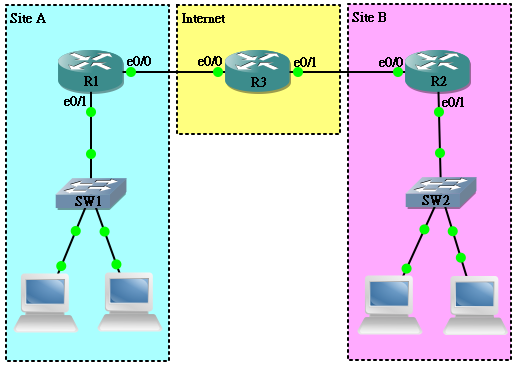
Router 的起始设定如下:
hostname R1 ! interface Ethernet0/0 ip address 192.168.13.1 255.255.255.0 ! interface Ethernet0/1 ip address 192.168.10.1 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 192.168.13.3
hostname R2 ! interface Ethernet0/0 ip address 192.168.23.2 255.255.255.0 ! interface Ethernet0/1 ip address 192.168.20.1 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 192.168.23.3
hostname R3 ! interface Ethernet0/0 ip address 192.168.13.3 255.255.255.0 ! interface Ethernet0/1 ip address 192.168.23.3 255.255.255.0
所以,R1 能够 Ping 通 192.168.23.2,但就去不到 192.168.20.1,因为我们假设 192.168.10.0 / 24 和 192.168.20.0 / 24 都是 Internal IP。
R1#ping 192.168.23.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.23.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 24/49/92 ms R1# R1#ping 192.168.20.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds: UUUUU Success rate is 0 percent (0/5)
Step 1: 设定 Interesting Traffic
所谓 Interesting Traffic 就是需要建立 VPN 的 Traffic,在本例子中,R1 的 Interesting Traffic 就是由 192.168.10.0 / 24 到 192.168.20.0 / 24 的 Traffic,而 R2 则刚好相反,是由 192.168.20.0 / 24 到 192.168.10.0 / 24,我们用 Access List 把这些 Traffic Define 好。
R1(config)#ip access-list extended VPN-Traffic R1(config-ext-nacl)#permit ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 R1(config-ext-nacl)#exit
R2(config)#ip access-list extended VPN-Traffic R2(config-ext-nacl)#permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255 R2(config-ext-nacl)#exit
Step 2: 设定 IKE Phase 1 参数
R1(config)#crypto isakmp policy 1 !encryption 可使用 DES, 3DES 或 AES,其中以 AES Security 最高 R1(config-isakmp)#encryption aes !hash 可选 SHA 或 MD5,SHA Security 较高 R1(config-isakmp)#hash md5 !用 Pre Share Key 的方法来认证对方 R1(config-isakmp)#authentication pre-share !DH Group 用作产生 Symmetric Key,一般使用 Group 2 R1(config-isakmp)#group 2 !管道的 Lifetime,预设为 86400 R1(config-isakmp)#lifetime 30000
R2(config)#crypto isakmp policy 1 R2(config-isakmp)#encryption aes R2(config-isakmp)#hash md5 R2(config-isakmp)#authentication pre-share R2(config-isakmp)#group 2 R2(config-isakmp)#lifetime 30000
Step 3: 设定 IKE Phase 2 参数
可以在 AH Transform 选择一款,在 ESP Cipher 选择一款,在 ESP Auth 选择一款,基本上选用越多就越安全但比较耗资源。最後选择是否要做 Compression。所以最多可选 4 个 Option。无论选多少个,两边 Peer 的选择必需相同。
R1(config)#crypto ipsec transform-set TS ? ah-md5-hmac AH-HMAC-MD5 transform ah-sha-hmac AH-HMAC-SHA transform comp-lzs IP Compression using the LZS compression algorithm esp-3des ESP transform using 3DES(EDE) cipher (168 bits) esp-aes ESP transform using AES cipher esp-des ESP transform using DES cipher (56 bits) esp-md5-hmac ESP transform using HMAC-MD5 auth esp-null ESP transform w/o cipher esp-seal ESP transform using SEAL cipher (160 bits) esp-sha-hmac ESP transform using HMAC-SHA auth
R1(config)#crypto ipsec transform-set TS esp-3des ah-sha-hmac
R2(config)#crypto ipsec transform-set TS esp-3des ah-sha-hmac
假设以 ccie 为 Pre-share Key。
R1(config)#crypto isakmp key 6 ccie address 192.168.23.2
R2(config)#crypto isakmp key 6 ccie address 192.168.13.1
Step 5: 定义 Crypto Map
把我们刚才设定的东西,一次过放进 Crypto Map 之中。最後把 Crypto Map 放上 Interface。
R1(config)#crypto map CMAP 1 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. R1(config-crypto-map)#set peer 192.168.23.2 R1(config-crypto-map)#set transform-set TS R1(config-crypto-map)#match address VPN-Traffic R1(config-crypto-map)#exit R1(config)#interface ethernet 0/0 R1(config-if)#crypto map CMAP
R2(config)#crypto map CMAP 1 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. R2(config-crypto-map)#set peer 192.168.13.1 R2(config-crypto-map)#set transform-set TS R2(config-crypto-map)#match address VPN-Traffic R2(config-crypto-map)#exit R2(config)#interface ethernet 0/0 R2(config-if)#crypto map CMAP
测试
在 R1 尝试让 192.168.10.1 去 Ping 192.168.20.1,已经可以 Ping 通了。
R1#ping 192.168.20.1 source 192.168.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.20.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.10.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 36/72/96 ms
R1#show crypto isakmp sa
dst src state conn-id slot status
192.168.23.2 192.168.13.1 QM_IDLE 1 0 ACTIVE
R1#show crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: CMAP, local addr 192.168.13.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0)
current_peer 192.168.23.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 192.168.13.1, remote crypto endpt.: 192.168.23.2
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xD2E73BB1(3538369457)
inbound esp sas:
spi: 0x80CE4FB7(2161004471)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4531862/3488)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
spi: 0x490FFB61(1225784161)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4531862/3481)
replay detection support: Y
Status: ACTIVE
inbound pcp sas:
outbound esp sas:
spi: 0xD2E73BB1(3538369457)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4531862/3481)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
spi: 0x4F72667D(1332897405)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4531862/3479)
replay detection support: Y
Status: ACTIVE
outbound pcp sas:
相關主題
Jan Ho 2021-07-22
Posted In: 虚拟私人网路 VPN
发表回复